SMART Blog
Give Tech Security Credit When Credit Is Due
 We talk a lot about viruses or holes in supposedly sound security structures, but today it seems as if that's all there is to talk about. It's all about the latest vulnerability, or a hacking attack that left millions of people with compromised passwords. People always concentrate on the negative aspects of things without looking at the positives.
We talk a lot about viruses or holes in supposedly sound security structures, but today it seems as if that's all there is to talk about. It's all about the latest vulnerability, or a hacking attack that left millions of people with compromised passwords. People always concentrate on the negative aspects of things without looking at the positives.
But, regardless of this, security has come a long way since the dawn of the Internet. In light of all of the nasty things online, it might be time to celebrate some of the greater achievements in security technology.
More Secure Security Defaults
Back in the days before the Internet was such a dangerous place, companies thought little about ensuring their systems were secure, and concentrated more on a user-friendly experience. This meant that companies would opt for security default prompts that were easier to understand, but less secure. A lot of the time, these default prompts would make the system much more vulnerable to outside threats.
An example of this is the macro virus. When it first appeared, nearly all office applications auto-ran it, or rather, prompted the user to decide whether they wanted to run the macro or not. All the user needed to do was hit the Enter key, and bam. Infected. However, now most software has much better security defaults, and the software will prompt the user to select the default option, which is now the secure choice.
Improved Drive Encryption
Perhaps one of the best things that could have happened to hard drives is data encryption. What's even better is that this feature is enabled without you even noticing that it is happening. This ensures that your hard drive is protected in the event of an attack. In fact, drive encryption is the default choice on many computers, including those running Windows 8 with BitLocker Disk Encryption.
Encrypted hard drives make it harder for thieves to steal your data if they get ahold of your laptop. The data encryption doesn't normally affect the end-user (although it can make recovering data harder for technicians, but the ends justify the means).
Two-Factor Authentication is More Important Than Ever
Two-factor authentication is a great security measure that is designed to protect your identity. Generally, what this entails is the input of a password, plus either a PIN number or some other form of identification via a mobile device. An example of this is entering a password, which prompts the site to send a SMS message to your phone. This message will have a secondary code needed to access the site. This prevents hackers from getting into your personal information if they don't have physical access to your phone.
Default to SSL/TLS
The pioneer of encrypted Web services, Google, has led most popular cloud services and email providers to enable automatic SSL (Secure Socket Layer) encryption, which was later replaced by TLS (Transport Layer Security). These types of encryption are designed to authenticate the party who is on the receiving end of the sent information, and then share a secret key between the two parties which is used to encrypt and decrypt the information sent.
Previously, SSL/TLS had to be specifically enabled by the user or simply wasn't available for certain sites, which meant that insecurity and theft of passwords and cookies was commonplace. While hardware was significantly slowed down in past years by encryption technology, that is no longer the case, and it has become less of an issue. But, if the Heartbleed bug taught us anything, it's that SSL isn't a guaranteed security solution, and that we should always make sure that the URL we are visiting is safe and keep our passwords secure. In order to check the security certificate of a website, look for the padlock symbol next to the URL in the address bar.
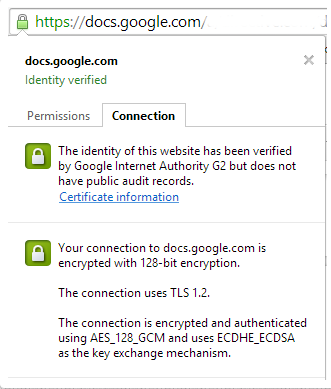
You can then view the security certificate information for that site, and ensure that the site's identity is known and that it is secure. You can also look in the URL for the "s":
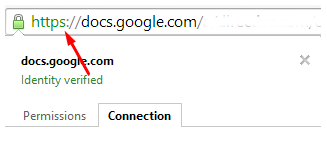
If this "s" is present at the beginning of the URL, the site is securely encrypted, and you don't need to worry too much what you are sending them.
If you feel like your business isn't taking advantage of this new security technology to its best potential, call SMART Services at 586 258-0650 . We'll focus on taking care of your important data so that you can reap the benefits of these security advances!




Comments