 When tech support is done right, it can be a beautiful service. When tech support is done poorly, it will only add stress to an already frustrating problem. You know that we provide excellent tech support, but if you are seeking support for a technology that we don't cover, then you may think you'll run into obstacles.
When tech support is done right, it can be a beautiful service. When tech support is done poorly, it will only add stress to an already frustrating problem. You know that we provide excellent tech support, but if you are seeking support for a technology that we don't cover, then you may think you'll run into obstacles.
SMART Blog
 Servers are one of most powerful pieces of equipment in the office, but that does mean they are the toughest. The hard drives in servers are made up of ridiculously fast moving parts. One day, these small parts will fail and end the server's life with a sudden crash. Here are a few steps you can take to prepare for server doomsday.
Servers are one of most powerful pieces of equipment in the office, but that does mean they are the toughest. The hard drives in servers are made up of ridiculously fast moving parts. One day, these small parts will fail and end the server's life with a sudden crash. Here are a few steps you can take to prepare for server doomsday.
 Desktop Virtualization is a great solution that lets you run two operating systems simultaneously on one computer. This allows users to no longer be tied down by one machine, and it can save your company money by cutting back hardware expenses. Local and Client/Server are the two models of Desktop Virtualization; here's how they compare.
Desktop Virtualization is a great solution that lets you run two operating systems simultaneously on one computer. This allows users to no longer be tied down by one machine, and it can save your company money by cutting back hardware expenses. Local and Client/Server are the two models of Desktop Virtualization; here's how they compare.
 It takes a big person to admit when they're wrong, and there's nothing bigger than Microsoft. Windows 8 hasn't sold like Microsoft anticipated, and users pin the blame solely on one little button, the Start button, or the lack thereof. With Windows Blue (officially previewing June 26), it's rumored that Microsoft is remorsefully bringing back the button.
It takes a big person to admit when they're wrong, and there's nothing bigger than Microsoft. Windows 8 hasn't sold like Microsoft anticipated, and users pin the blame solely on one little button, the Start button, or the lack thereof. With Windows Blue (officially previewing June 26), it's rumored that Microsoft is remorsefully bringing back the button.
There was a time when tape backup was the cheapest and the standard data backup solution for businesses. Over the years, cloud services have become more affordable, and now cloud backup solutions like a BDR are cheaper and give businesses more security features. If you are still backing up with tape, then you may be losing money and even putting your business at risk!
With all the attention that hackers receive, you would think that they are solely responsible for every network security breach, but the truth of the matter is that most damages to company networks are due to negligence. Here are the four most common IT security oversights that can lead to major damages to your network.
 Working in front of a computer all day can be challenging for your mind, but not very stimulating for your body. Anything physical that you can add to your routine will benefit your health and stave off the negative side effects that come from sitting in one place for too long. Stretching is a great and easy way to get physical, and yes, there is an app for that.
Working in front of a computer all day can be challenging for your mind, but not very stimulating for your body. Anything physical that you can add to your routine will benefit your health and stave off the negative side effects that come from sitting in one place for too long. Stretching is a great and easy way to get physical, and yes, there is an app for that.
 The risk of flooding affects many people, not just the ones who own riverside property. Rivers are prevented from flooding by a system of man made levees. Many of these levees were built many generations ago to protect farmland. Overtime, farms turned into suburbs, levees deteriorated, and governments cut levee maintenance budgets; these factors have all contributed to increase people's risk of flooding.
The risk of flooding affects many people, not just the ones who own riverside property. Rivers are prevented from flooding by a system of man made levees. Many of these levees were built many generations ago to protect farmland. Overtime, farms turned into suburbs, levees deteriorated, and governments cut levee maintenance budgets; these factors have all contributed to increase people's risk of flooding.
 The IT industry is such a rapidly changing field that it can take up a fair amount of your time just to keep up with all of the latest developments. Staying current translates into a lot time visiting tech news websites and reading gadget reviews. You are a busy person, is it worth it to spend your time keeping up with technology?
The IT industry is such a rapidly changing field that it can take up a fair amount of your time just to keep up with all of the latest developments. Staying current translates into a lot time visiting tech news websites and reading gadget reviews. You are a busy person, is it worth it to spend your time keeping up with technology?
 Running a business today comes with the responsibility of minimizing your company's impact on the environment. This means taking a second look at traditional business models and finding better ways that minimize waste. One big step that your business can take towards going green is to migrate your traditional IT services over to the cloud.
Running a business today comes with the responsibility of minimizing your company's impact on the environment. This means taking a second look at traditional business models and finding better ways that minimize waste. One big step that your business can take towards going green is to migrate your traditional IT services over to the cloud.
Emotions aside, whenever an employee is fired or quits, their departure means extra paperwork for Human Resources. After the farewell cake has been cleaned up, the exit interview has been completed, and all the resignation forms have been filed, it is now vital that the former employee's access to the company's network be completely removed.
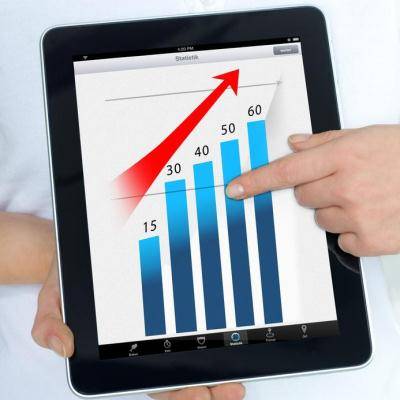 It doesn't always take a huge investment to improve your bottom line. Performing routine upgrades or adding a single piece of equipment can make operations much smoother, and in the end, more profitability. Here's a list of a few relatively simple upgrades to your IT infrastructure that make a huge difference!
It doesn't always take a huge investment to improve your bottom line. Performing routine upgrades or adding a single piece of equipment can make operations much smoother, and in the end, more profitability. Here's a list of a few relatively simple upgrades to your IT infrastructure that make a huge difference!
 For most of the last decade the telecommunications company Research in Motion (RIM) led a worldwide smartphone charge with it's series of Blackberry devices. In the past two years, however, RIM's revenue stream has been cut in half and their staggering profits have turned into substantial losses. Can anything save this struggling company?
For most of the last decade the telecommunications company Research in Motion (RIM) led a worldwide smartphone charge with it's series of Blackberry devices. In the past two years, however, RIM's revenue stream has been cut in half and their staggering profits have turned into substantial losses. Can anything save this struggling company?
 When it comes to running a business, having great software and hardware and a properly configured network infrastructure is important. Technology has changed the way the world gets work done, communicates, and even has fun. We love technology, gadgets, and having toys to play with; it's our passion. However, we feel it's important to say that technology isn't everything.
When it comes to running a business, having great software and hardware and a properly configured network infrastructure is important. Technology has changed the way the world gets work done, communicates, and even has fun. We love technology, gadgets, and having toys to play with; it's our passion. However, we feel it's important to say that technology isn't everything.
 When you mention the term 'disaster recovery,' most people think about the big ground-shattering events like earthquakes, fires, floods, tropical storms, etc. While these natural events are certainly disasters and devastating in their own right, smaller things can constitute as a disaster for your business, and they aren't seasonal. 99% of disasters happen in the office, most are server failures or some type of data loss.
When you mention the term 'disaster recovery,' most people think about the big ground-shattering events like earthquakes, fires, floods, tropical storms, etc. While these natural events are certainly disasters and devastating in their own right, smaller things can constitute as a disaster for your business, and they aren't seasonal. 99% of disasters happen in the office, most are server failures or some type of data loss.
 The Internet certainly has changed the way we live, work, shop, and communicate. We may think we're superior to previous generations because of all our Internet-based technology, but we have video proof that the Internet was actually conceptualized in 1969. In many ways, our parents and grandparents were spot on with their predictions. In other ways, not so much.
The Internet certainly has changed the way we live, work, shop, and communicate. We may think we're superior to previous generations because of all our Internet-based technology, but we have video proof that the Internet was actually conceptualized in 1969. In many ways, our parents and grandparents were spot on with their predictions. In other ways, not so much.
Here are some basic steps you can take to improve the security of your iPad.
Configure mobile devices securely.
Some simple configurations can aid in the security of your iPad. Enable password authentication, ensure SSL protection is enabled, utilize remote wipe capabilities, and avoid using auto-complete features that remember user names and passwords.
Connect to secure Wi-Fi networks.
Avoid joining unknown Wi-Fi networks.
Update mobile devices frequently.
Be sure to maintain up-to-date software including operating systems and applications.
Utilize anti-virus programs and configure automatic updates if possible.
Just as your PC should have a proper anti-virus solution, your mobile devices should be equipped with anti-virus protection where possible.
Use an encryption solution to keep portable data secure in transit.
If confidential data must be accessed or stored, make sure users have installed an encryption solution.
Properly wipe devices and dispose of properly.
Get your device properly wiped – don’t just pitch it!
Develop guidelines for acceptable iPad and mobile device usage.
Additionally, there are solutions that allow you to secure and manage multiple devices that include functionality like device tracking, profile management, and preventing unauthorized app downloads. One such solution is SMARTmobile Security from SMART I.T. Services. Contact us to learn more about how to secure your mobile devices and make managing them a breeze with SMARTmobile Security.
We all have our preferences when it comes to how we work. Our Microsoft Outlook settings are no different.
Many people like to have their inbox set up with the reading pane to preview emails at a glance without fully opening them. This is a common practice that, unfortunately, opens up users for unwanted viruses and threats via email.
Emails sent to your inbox containing viruses or malware will install the threats when the emails are viewed in the preview pane, whether or not you've fully opened them or not.
To avoid this potential danger, simply turn off your Outlook reading pane. To do this, go to View > Reading Pane > Off.
This should be done for Outlook Web Access as well because the threat is the same.

The Health Information Technology for Economic and Clinical Health (HITECH) Act, passed as part of American Recovery and Reinvestment Act of 2009 (ARRA), calls for protected health information (PHI) to be rendered unreadable and unusable.
Encryption is a logical and easy way to protect client information sent via email. There is a lot of confusion on the subject, so we have setup a page on our website with more information about HIPAA and HITECH compliance.
While you're there, you can learn about the solution we offer to help you achieve compliance.
Learn more.

The longest running state agent technology conference in the nation, Great Lakes Automation Day (GLAD) was presented by the Michigan Association of Insurance Agents on November 11, 2010.
The event drew over 150 agents to hear presentations from agents on the leading edge of technology, carrier technology representatives, agency IT leaders, and more. GLAD’s day-long format was topped-off with numerous vendor booths and wonderful networking opportunities.
Steve Brooks of B & B Premier Insurance Solutions kicked off the day with his keynote presentation regarding the latest tools and opportunities for agents to grow their personal lines business, despite intense competition from captive and direct agents.
Mike Steger, Communications Manager at Michigan State University, followed with a fast-paced session that highlighted 45 technology tips in a mere 45 minutes. His presentation included a slew of websites and resources, most of which are free to agents, which can be used for improving online presence, productivity, and more.
After two additional sessions and a delicious lunch, Jerry Fetty took the Kellogg Center stage to present Mobile Computing Today. Jerry discussed the latest developments and reviewed a variety of devices, emphasizing the need to understand how agents plan to work remotely in order for them to select the mobile platform and device that will allow them to be the most productive.
A concurrent Michigan NetVU user group meeting rounded out the information-packed day.
Thank you to everyone who stopped by the SMART I.T. Services and MySalesResults booths and congratulations to Ashley Whitney of Harbor Brenn Insurance Agency, winner of our raffle for an Archos 2.8 internet tablet device. We hope to see you all again at the MAIA’s Annual Convention on February 22-24, 2011 in Mt. Pleasant, Michigan!




